Introduction:
In the digital age, securing your API is as crucial as its service. FastAPI, a modern Python web framework for building APIs with Python 3.7+ using standard type hints, is at the forefront of facilitating secure and fast API development.
This blog, brought to you by August Infotech, a leader in custom python web solutions, will guide you through implementing token-based authentication in FastAPI, a method lauded for effectiveness and API security. By the end of this comprehensive guide, you’ll have a robust understanding of safeguarding your FastAPI projects, establishing August Infotech as a beacon of knowledge and authority in the field.
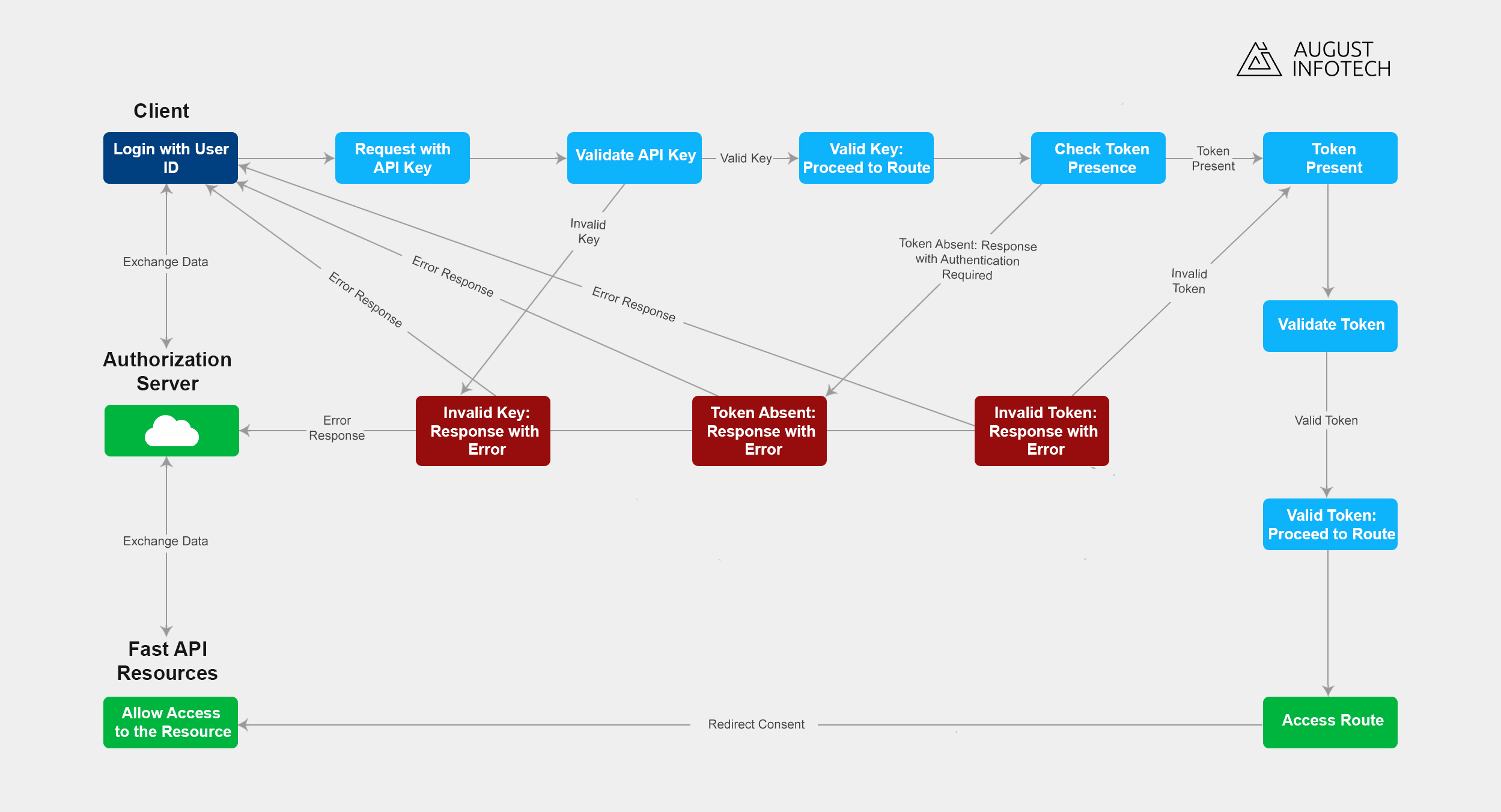
Table of Contents:
1. Understanding authentication in FastAPI:
Delve into the world of FastAPI and its support for various authentication methods, including API keys, OAuth, and bearer tokens — setting the stage for a deeper exploration of token authentication. We’ll mainly focus on token-based authentication, discussing its benefits and why it’s a preferred choice for many developers, touching on the foundational API security principles and token authentication benefits.
2. Setting up FastAPI project:
Kickstart your project the right way. This section will walk you through creating a FastAPI project, advising on the optimal directory structure and virtual environment setup. We’ll provide a step-by-step guide to ensure your development environment is up to the task, laying a solid foundation for secure, scalable API development.
3. Generating a secret key:
Discover the significance of a secret key in your authentication system. We’ll guide you through generating a robust private key and discuss best practices for keeping it secure. This key will be the cornerstone of your token-based authentication, used to sign and verify tokens, ensuring only authorized users access your API.
4. User model and token schema:
Understand how to represent your users and their credentials within your system. We’ll cover defining a User model and a Token schema, which is essential for parsing, validating tokens, and managing user data. Learn how to to structure this data to streamline authentication processes effectively and enhance security. This approach is part of the white label web development services offered by August Infotech, ensuring a tailored solution for clients.
5. Authentication dependency:
In FastAPI, dependencies are a powerful feature for reusing code. We’ll create a dependency function that acts as a middleware for your routes, handling the authentication by decoding and verifying tokens. This section will demonstrate how to abstract complex authentication logic, making your code cleaner and more maintainable.
6. Token generation and validation:
Tokens are the lifeline of your authentication system. Learn the ins and outs of generating secure tokens and the methods for validating them. We’ll discuss different types of tokens, their life span, and how to handle token renewal, ensuring your API’s security is airtight.
7. User authentication endpoint:
Every secure API needs a reliable authentication endpoint. Here, we’ll build an endpoint where users can obtain a token by providing their credentials. This section will guide you through handling login requests, issuing tokens, and setting up necessary validations, reflecting the user authentication best practices.
8. Securing endpoints with authentication:
With the mechanics of token generation and user authentication covered, it’s time to secure your API endpoints. Learn how to use the Depends function and the get_current_user dependency to protect your resources, discussing strategies for API endpoint security and user access management, along with API security best practices for resource protection.
9. Securing against unwanted hits:
Unwanted access can lead to system overload and potential security breaches. We’ll discuss how requiring tokens for authentication acts as a first line of defense, preventing unauthorized access and ensuring that only users with valid tokens can interact with your API.
10. Securing against data injection:
Data injection is a common threat. Explore how token-based authentication secures your API against such attacks. By ensuring that tokens are generated and verified using a secret key, you add an extra layer of validation, making it significantly harder for attackers to inject malicious data.
11. Testing authentication:
Testing is a critical component of any security strategy. We’ll cover how to use tools like Curl or Postman to simulate authentication requests and validate your endpoints’ security. Learn how to test various scenarios, ensuring your authentication process is robust and ready for deployment.
Conclusion:
In this FastAPI Security Guide, we’ve journeyed through setting up a secure API with FastAPI, focusing on token-based authentication. Remember, the security of your API is not just about protecting data; it’s about fostering trust with your users. By implementing the strategies discussed, you’re not just coding; you’re crafting a secure gateway to your services. As a leading offshore development company known for custom Python solutions and white-label web development services, August Infotech is committed to delivering excellence in every aspect of secure API development.






